Indianapolis, Indiana — According to President Biden, businesses should be prepared for Russian President Vladimir Putin to directly target the U.S. through cyberattacks on businesses and critical infrastructure.
President warned that these attacks could come as retaliation for the economic sanctions placed on Russia by the U.S. and its allies.
According to Aaron Pritz, a cybersecurity expert and the CEO of Reveal Risk, he’s heard some concern from clients since Biden’s warning. “The attention and calls that we get and focus that we’ve been spent, spending time on helping companies prepare, is high, but it’s been eerily quiet,” Pritz said.
Pritz provided I-Team 8 with some helpful hints for businesses or companies wanting to prepare for not just a Russian cyberattack, but any kind of cyberattack.
Pritz’s suggestions include:
• Create a response plan: It’s significantly less stressful for companies when they’ve already come up with a plan of action if a cyberattack were to happen.
• Invest in employee training: People are the first target of cyberattacks. This often happens through scams on social media, phishing emails, or fake friend requests.
• Update servers and IT equipment: If you work with a lot of technology, it’s important to get the most recent updates.
• Third-party risk management: If you often work with other companies in your business, make sure those companies have protection against cyberattacks so that if one occurs, it doesn’t spill over into your business.
• Identify the ‘Crown Jewels’: Identify the ‘Crown Jewels’ — the things within your company that would be most critical if compromised by a cyberattack.
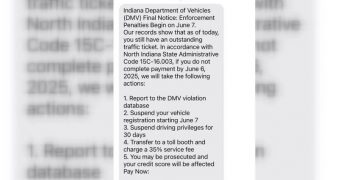
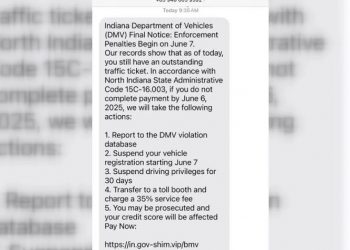
“For the average Hoosier, I think the plan is, be really careful when you’re interacting, that validating that messages are real,” Pritz said. “Everyone is kind of posturing and waiting and [there’s] no time like the present to get prepared, even if you’re doing the minimum basics.”
The Cybersecurity & Infrastructure Security Agency has also published alerts on their page to look out for, as well as a list of known exploited vulnerabilities.